ZeroTrust
Ensuring no implicit trust, requiring verification from anyone trying to access resources within a network, regardless of their location or network connection


Continuous Verification
Regularly verifying the identity and security posture of users, devices, and applications, irrespective of their location or network connection
Continuously verifying the authenticity of users, devices, and applications, ensuring ongoing security validation. Consistent and real-time monitoring of the security posture of entities, allowing for immediate response to any deviations.Removing the assumption of trust based on location or network connection, fostering a security approach that adapts to diverse environments.
Adapting and responding to changes in user behavior, device status, or application characteristics to maintain a proactive and resilient security stance

Least Privilege Access
Restricting access permissions to the bare minimum required for specific tasks, minimizing potential exposure to security threats
Grant individuals or systems the minimum level of access required to perform their specific tasks, reducing the risk of unauthorized activities. Implement detailed access controls to restrict users to the precise resources or data necessary for their job functions, minimizing potential security vulnerabilities.
Conduct periodic reviews of access permissions, adjusting them based on job roles and responsibilities to ensure alignment with current business needs. By limiting access to the essential elements, Least Privilege Access helps fortify the overall security posture of an organization, preventing unnecessary exposure to potential threats.
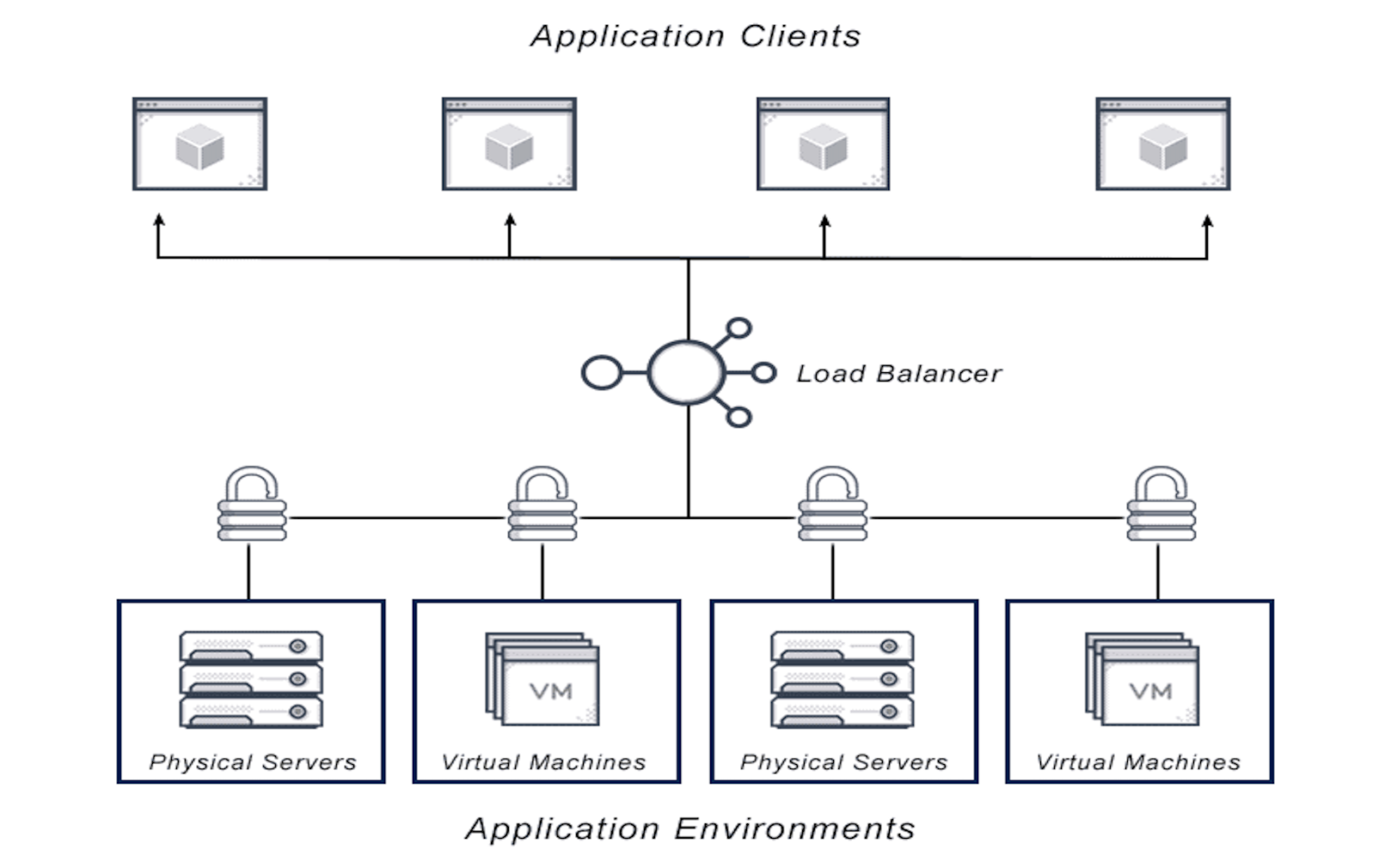
Micro-Segmentation
Implementing network segmentation at a granular level to isolate and protect individual workloads, applications, or data
Segregating the network into small, isolated segments to contain and restrict lateral movement of threats within the infrastructure. Implementing precise access controls at a granular level, allowing organizations to define and enforce specific security policies for individual workloads or applications.
Minimizing the potential impact of security breaches by limiting access to sensitive data, applications, or systems, thereby reducing the overall attack surface. Optimizing network performance by directing and isolating traffic based on specific criteria, enhancing overall efficiency and resource utilization.

Continuous Monitoring and Analytics
Employing real-time monitoring and advanced analytics to detect and respond to security threats promptly, ensuring ongoing situational awareness.
Ongoing and immediate observation of network activities, user behavior, and system events to detect potential security threats in real time. Utilization of sophisticated analytical tools and algorithms to assess patterns, anomalies, and trends within the monitored data, enhancing the ability to identify and respond to security incidents.
Integration of up-to-date threat intelligence feeds to enhance the understanding of emerging cybersecurity threats, providing context for monitoring activities. Empowering organizations to respond proactively to security incidents by leveraging insights gained from continuous monitoring and analytics, thereby minimizing the impact of potential breaches.